This essay introduces Configure-Able methods as a means to re-value recommender systems (RS), bringing together STS, software studies and crip studies to produce a generative toolset to help imagine and achieve radical new abilities for infrastructures. Configure-Able methods enable us to negotiate the socio-political relations of infrastructure, examining their imaginaries in dialogues with their matterings to display disparities in their realities, but more importantly as a toolset to generate and enable alternatives. Taking RS as a case study this project aims to use configure-able methods to examine their histories, philosophies and matterings, and imagine new configurations informed through open-software, intersectional critiques and material knowledges.
Recommender systems, Crip Studies, Trans*Feminism, Software Studies, Science Technology Studies, Social Sciences, AI, Reinforcement Learning, Configure-Able Methods.
Configure-able methods are rooted in the work of enabling intersectional4 criptiques into the methods and imaginaries of sociotechnical systems, at its core asking how these knowledges can help us transform relations of control into ones of care and self-exploration enabled through life affirming infrastructures5. Informed by the radical work of Sins Invalid (2015) (Fig.1) and Healing Justice London (2022), transforming community and disability justice through the voices, experiences and methods of those living through it. Following this agenda, configure-able methods aim to be a generative toolset to reconfigure sociotechnical infrastructures into ones that can be led from their subject and not from a generalized and prescribed overview. This reconfiguring toolset aims to transform the imaginaries of a big tech into minor, subjective, and dynamic ones, which can enable the people within them to have new agencies over what their community infrastructures are imagined as and how this comes into being.

Recommender Systems (RS), the case study of this essay, are one of the most used intersections with media on cloud platforms6, producing addictive selections of media (Chun 2016) you didn’t know existed and making the unfathomable challenge of exploring the abundance of cloud media possible. RS does this through automated valuing, sorting, ordering, and breaking down the mass of cloud data into hierarchies and comparative assemblages (Noble 2018) reinforcing how we imagine relationships as essentially comparative and hierarchical. The more classic and clear examples of these hierarchies are the likes of Noble’s critique of google rank, where results are ranked within a linear list, from most valued to least, but with the likes of talkative search engines (GPT utilized by Bing), and the complex animatic dynamics of feeds these hierarchies are being performed through new complex and less transparent forms which I will attempt to critique and re-value through configure-able methods.
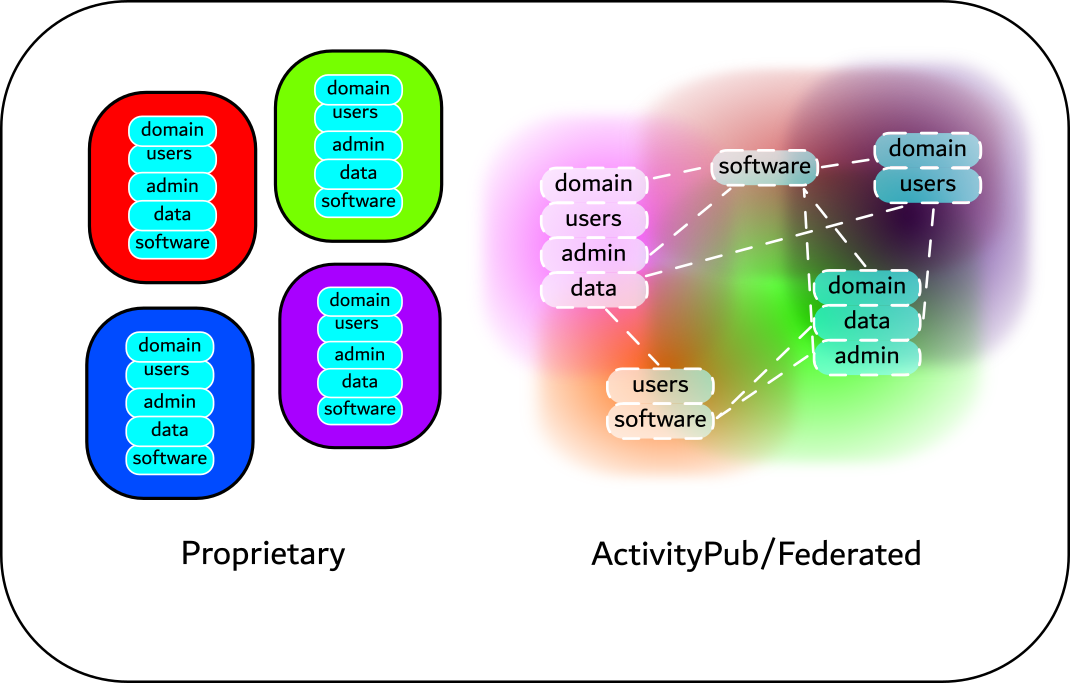
The current configuration of media platforms and their RS algorithms are performed through monolithic process of control and ownership, giving them greater agency within the social/political relationality of ability in their network. Their socio-technical infrastructures do this by gatekeeping, augmenting and ordering our experience and representation of the world through them. These monolithic configurations of platforms are currently being (have always been) challenged by open and free software commoning of potential other configurations. One of the predominant examples, especially after the twitter takeover, is Mastodon on the activity pub protocol, providing an infrastructure to create decentralized7 and federated8 networks and communities. Through these new configurations you see how there is a shift within the political/ relational model of ability (Kafer 2013) within the infrastructure, enabling the people using it to configure and form their communities to their needs and desires. This shift moves away from the gatekeeping and extractivist methods of corpo-social platforms to ones that enable people to control their data, move their accounts to different servers9, use the same data between different platforms or access it from different software10. Most importantly this relationship creates a space where people can develop their own abilities to create communities and places safe from infrastructural inequality and harm11. This reformation of infrastructure to enable people to define their own configuration of imaginaries and their matterings is a prime example of what I am calling configure-able methods.
Much like Chun and Barnett’s analysis of Latent vectors17 (Chun and Barnett 2021), RL systems are configured not only through imaginaries and the language of segregation, exploitation, and extraction, but also mathematic principles such as optimal control. In many AI systems, optimal control is embodied in their configuration, but is implemented through their loss function. Loss values the performance of a system to then tweak its potentially many thousands to billions of parameters towards an optimal outcome. Loss as a metaphor figures these complex dynamics into singular narratives of prospective loss and gains (economically) which can be navigated through Ferreira da Silva’s (2016; 2017) analysis of efficient causality18. She traces this thread through Newton, Descartes and Galileo, and sees it extracted from the rest of Aristoteles' four causalities (Falcon 2023). This configuration of efficient logics relies on the functionalities of mathematics to legitimize claims, instead of accounting for the whole, or final cause. Through this reductionist approach algorithms are only legitimized if they work, and not through a more complex relation of how they work, and what effect they may have on the environment around them. The legitimizing mathematics of the loss function that “work” are defined by rather rudimentary logics of differencing19, how far spatially and geometrically is the “truth” from the action, often squared to exaggerate differences and clearly define outliers. Through configure-able methods we must question these outdated and destructive dynamics to then imagine how we could configure these infrastructures otherwise (Ferreira da Silva 2016; Pritchard 2018; Soon and Cox 2021), implementing contemporary STS, social science, crip trans*feminist and intersectional approaches and models into their configuration.
Stepping into these technologies through configure-able methods I have developed a criptique of the “cherry on the cake” (LeCun 2016) of RS and predictive AI, reinforcement learning (RL). The metaphor of the cherry on the cake for LeCun, Facebook's VP and Chief AI Scientist, represents the ability for RL to transform the bulk of intelligent systems (the cake) into adaptable ones that can take on a wider set of unknowns. This is amplified by both Google and OpenAI engineers suggesting that RL powered models are the most likely step into sentience or unified/general intelligence. The cherry and its stone here can be re-read as a metaphor for RL as the element that will bring this trained body of (un)supervise NNs into life. It is clear that RL is imagined as the keystone to sentient intelligence, this being recently reinforced by RL’s amazing abilities within LLMs15 like GPT models, but what do the concepts these systems are based on say about them? And how could we implement them otherwise?
RL itself is founded around the criticized concepts of animal learning (Fig. 3) by Edward Thorndike (1898), which configures a penal system of roles for animals or agents alike, where good behaviors are rewarded with freedom and nourishment and bad ones lead to the subject being incarcerated or punished until they get it right. RL here symbolizes the Promethean imaginary of platform and cloud capitalism (Ferreira da Silva 2016; Parisi and Ferreira da Silva 2021), the escaping from enslaved and obscure nature into ordered freedom16. These implementations of penal logic have formed powerful dynamics within intelligent systems, but are very limited due to their reductive description of their problem spaces and environment through a simplistic reward (penal) system, often just one or few dimensions in description. If we also take a look at the language and metaphors (Cowan and Rault 2022) used to describe RL in practice it orientates wordings like “exploration vs exploitation”, “maximize reward” and “Greedy Policies”, reinforcing extractivist imaginaries for these technologies to play out.

Much like Chun and Barnett’s analysis of Latent vectors17 (Chun and Barnett 2021), RL systems are configured not only through imaginaries and the language of segregation, exploitation, and extraction, but also mathematic principles such as optimal control. In many AI systems, optimal control is embodied in their configuration, but is implemented through their loss function. Loss values the performance of a system to then tweak its potentially many thousands to billions of parameters towards an optimal outcome. Loss as a metaphor figures these complex dynamics into singular narratives of prospective loss and gains (economically) which can be navigated through Ferreira da Silva’s (2016; 2017) analysis of efficient causality18. She traces this thread through Newton, Descartes and Galileo, and sees it extracted from the rest of Aristoteles' four causalities (Falcon 2023). This configuration of efficient logics relies on the functionalities of mathematics to legitimize claims, instead of accounting for the whole, or final cause. Through this reductionist approach algorithms are only legitimized if they work, and not through a more complex relation of how they work, and what effect they may have on the environment around them. The legitimizing mathematics of the loss function that “work” are defined by rather rudimentary logics of differencing19, how far spatially and geometrically is the “truth” from the action, often squared to exaggerate differences and clearly define outliers. Through configure-able methods we must question these outdated and destructive dynamics to then imagine how we could configure these infrastructures otherwise (Ferreira da Silva 2016; Pritchard 2018; Soon and Cox 2021), implementing contemporary STS, social science, crip trans*feminist and intersectional approaches and models into their configuration.

There is great power in the configure-ability of these analytic systems, of being able to perform them otherwise in new revealing formations. Examples of an iconic work that creatively reconfigures sociotechnical infrastructures is the likes of Joy Buolamwini’s Gender Shades (Buolamwini and Gebru 2018) using facial recognition AI analytics and a custom dataset to analyze the algorithm’s own racism and gender biases. There are also examples of infrastructures being formed through and empowering crip wisdom, with Melt forming ACCESS SERVER (Fig.5), which is an email server that anonymously mediates and financially compensates access requests20 that disabled people send towards cultural institutions. ACCESS SERVER reconfigures the awkward and labor inducing process of requesting access and enables both the person and the institution in this exchange. It enables the person requesting access by providing anonymity and a third party to talk through to ease the dialogue, while also compensating them for each email sent. It enables the institutions to create a freer flowing dialogue where they can hear about and improve their accessibility from those affected by it and, in this exchange, the ACCESS SERVER also tries to provide them with all of the resources to inform the change needed. Both of these works pulling from the artists/researchers lived experiences and only come into being through the nuances of their intersectional approaches.

So many of the tools to do these sorts of reconfiguring either lay within the complexities of code and its hierarchies of accessibility and understanding, where they may take years to learn and be able to implement, otherwise they are often very awkwardly arranged through predefined and limiting paid for and/or extractavist cloud platforms. Runway ML, one of the original for-profit creative AI tool platforms, is configured by taking open-source AI models and implementing them through their web interface, charging for the computation of the training of models and generating of content. The key here is that most accessible home machines and the people using them would not be able to train or run these algorithms, forcing most people to only enable them through some sort of cloud computing infrastructure. This can also be said about the creation of datasets for these models, which would be difficult and very laborious to produce if you did not use some web scrapping or other cloud extraction methods. This relational ability is again not primarily situated in one place, such as the hardware, but it is also inferred in the attitudes and politics of investors and developers focusing on the growth of these large-scale and inaccessible tools and infrastructures.
To practice configure-able RS I am coming together with my studio, Imaginary Practices (IP)21, to collaboratively develop different works to imagine through practice how RS and AI infrastructures might be configure-able. Informed by accessible and transformative AI projects, like Rebecca Fiebrink’s Wekinator (Fiebrink 2015) and Gene Kogan’s ML4A(Kogan 2016), this project aims to form new intersections into these mechanisms, enabling RS and AI to be configure-able to different imaginaries and mechanisms. The collaboration with IP has so far produced a few preliminary tests starting to form new tools and dynamics within AI infrastructures, but for this essay I will discuss two.

The first project is called the F*MNIST dataset, it is a dataset that we made collaboratively with a wide group of feminists, informed by Fermenting Data (Tyżlik-Carver, Rossenova, and Fuchsgruber 2022). Whilst forming the data we created a conversation, around what a dataset and data could be through feminist approaches. The work’s title itself is a play on the MNIST22 dataset, which is a standardized and normalized dataset that was/is a foundational benchmark for computer vision models. By F* the MNIST dataset we questioned what the standards of a dataset are and how we could renegotiate what normalizing this data could mean and how we contextualize these indexes of data so that they are not isolated and efficient images. To do this people inputting data were encouraged to be disruptive and unstandardized (whatever that meant to them), allowing space for people to add their own new indexes to the dataset (Fig. 5), as well as more information about themselves and the context of their input. This dataset is fluid and continually being added to and is formatted in linked open data (LOD) to create a complex web of data, relations and people in semantic triples that are open and linkable, which radically differ from the anonymous and isolated standards of the original MNIST.

The second work with IP is the re-reader, an outcome from an exercise imagining what roles AI can play within text analysis, communal reading, and research. We have been playing with a few different configurations, focusing on how highlighting and other preexisting affordances of digital reading can be made intelligent through small scale, local technologies that can help us renegotiate what we read. One of the most promising experiments from this work so far is an AI variational autoencoder23 that is trained from a local and small dataset of texts, compressing this set of knowledge into a three-dimensional latent space. This segregational latent space, which I mentioned Chun’s critique of, takes on a new form of non-prescriptive and performative, enabling the person to retrain it and reform its ontology and splitting of space. Once trained, this latent encoding or ontology is then used to highlight a text sentence by sentence to the color (RGB) determined by the three-dimensional latent encoding of that sentence (Fig. 6). This compositing of fluid and nondeterministic ontologies enables us to navigate texts simultaneously through these different dimensions and dynamics, the ones we read, and the ones re-read by the trained model and interpreted by us. The model used here is also lightweight and quick to run and train locally on most consumable computers.
These are two early attempts to enable AI and RS to be configure-able to different methods and, through these actions, we have realised that making RS and AI analytics configure-able also means to have their concepts, imaginaries and matterings adaptable and accessible too. To do this we have started to entangle these often siloed approaches into a collaborative wiki/docs alongside the code. By doing this we are attempting to enable ourselves to form new dialogues, metaphors and matterings in the creation of these works which can move beyond the efficient ones of contemporary AI. Configure-able methods here means for these intersections of language and practice to be generative re-imaginings of infrastructures. These methods bring with them not so many answers, but create space for questions and conversation around how these systems are configured and what that means for us as people and communities living within their political/relational modeling, enabling us to rethink, rename, remetaphorize and revalue their processes.
From this essay, we have seen the need for this change within RS, but the same is true in many other intelligent and future imagined tech infrastructures, as they need a deep rethinking and reapproaching. This project and its understanding of configure-able methods is very much at the beginning of its journey, but I see hope in this methodology and the radical agendas it grows from, as well as the promising steps made so far. It is a promising starting point for us, Imaginary Practice, to be able to begin this essential questioning of how we can configure these (intelligent) sociotechnical infrastructures otherwise.
Alexander, M. Jacqui. 2005. Pedagogies of Crossing: Meditations on Feminism, Sexual Politics, Memory, and the Sacred. Perverse Modernities. Durham [N.C.]: Duke University Press.
Aouragh, Miriyam, Seda Gürses, Femke Snelting, Helen V. Pritchard, and Jara Rocha. 2021. "Counter Cloud Action Plan: NEoN Digital Ethics Audit". 2021. http://titipi.org/?projects/digital-ethics-audit.
Benjamin, Ruha. 2016. "Racial Fictions, Biological Facts: Expanding the Sociological Imagination through Speculative Methods". Catalyst: Feminism, Theory, Technoscience 2 (2): 1–28. https://doi.org/10.28968/cftt.v2i2.28798.
———. 2019. Race after Technology: Abolitionist Tools for the New Jim Code. Medford, MA: Polity.
Bonhomme, Edna, Mario Guzman, Femke Snelting, and Pinar Tuzcu. 2020. "Bug Report: Tuning to Trans*feminist Xystem.Crash". 31 October 2020. http://meltionary.com/meltries/r.html.
Buolamwini, Joy, and Timnit Gebru. 2018. "Gender Shades". 2018. http://gendershades.org/.
Chance, Paul. 1999. "THORNDIKE’S PUZZLE BOXES AND THE ORIGINS OF THE EXPERIMENTAL ANALYSIS OF BEHAVIOR". Journal of the Experimental Analysis of Behavior 72 (3): 433–40. https://doi.org/10.1901/jeab.1999.72-433.
Chun, Wendy Hui Kyong. 2016. Updating to Remain the Same: Habitual New Media. MIT press.
Chun, Wendy Hui Kyong, and Alex Barnett. 2021. Discriminating Data: Correlation, Neighborhoods, and the New Politics of Recognition. Cambridge, Massachusetts: The MIT Press.
Cowan, Tl, and Jasmine Rault. 2022. ‘"Introduction: Metaphors as Meaning and Method in Technoculture". Catalyst: Feminism, Theory, Technoscience 8 (2). https://doi.org/10.28968/cftt.v8i2.39036.
Falcon, Andrea. 2023. "Aristotle on Causality". In The Stanford Encyclopedia of Philosophy, edited by Edward N. Zalta and Uri Nodelman, Spring 2023. Metaphysics Research Lab, Stanford University. https://plato.stanford.edu/archives/spr2023/entries/aristotle-causality/.
Ferreira da Silva, Denise. 2014. "Toward a Black Feminist Poethics: The Quest(Ion) of Blackness Toward the End of the World". The Black Scholar 44 (2): 81–97. https://doi.org/10.1080/00064246.2014.11413690.
———. 2016. "On Difference without Separability". Catalogue of the 32a São Paulo Art Biennial,‘Incerteza Viva’(Living Uncertainty), 57–65.
———. 2017. "1 (Life) ÷ 0 (Blackness) = ∞ − ∞ or ∞ / ∞: On Matter Beyond the Equation of Value’, e-flux journal no. 79 (February). https://www.e-flux.com/journal/79/94686/1-life-0-blackness-or-on-matter-beyond-the-equation-of-value/.
Fiebrink, Rebecca. 2015. "Wekinator 2.0". http://www.wekinator.org
Gumbs, Alexis Pauline. 2018. M Archive: After the End of the World. Durham ; London: Duke University Press.
Hamraie, Aimi, and Kelly Fritsch. 2019. "Crip Technoscience Manifesto". Catalyst: Feminism, Theory, Technoscience 5 (1): 1–33. https://doi.org/10.28968/cftt.v5i1.29607.
Healing Justice Ldn. 2022. "About. Healing Justice London (blog). 2022. https://healingjusticeldn.org/about/.
‘How to Apply This Recommender System for My Website? · Issue #1664 · Twitter/the-Algorithm’. 2023. GitHub. 5 April 2023. https://github.com/twitter/the-algorithm/issues/1664.
Kafai, Shayda. 2021. Crip Kinship: The Disability Justice & Art Activism of Sins Invalid. Vancouver: Arsenal Pulp Press.
Kafer, Alison. 2013. Feminist, Queer, Crip. Bloomington, Indiana: Indiana University Press.
Kogan, Gene. 2016. ‘ML4A’. https://ml4a.net/.
LeCun, Yann. 2016. ‘Predictive Learning’. Presented at the NIPS, December 5. https://nips.cc/Conferences/2016/ScheduleMultitrack?event=6197.
MELT. 2022. ‘Meltionary - ACCESS SERVER’. 31 March 2022. http://meltionary.com/accessserver.html.
‘ML | Common Loss Functions’. 2019. GeeksforGeeks (blog). 18 November 2019. https://www.geeksforgeeks.org/ml-common-loss-functions/.
Noble, Safiya Umoja. 2018. Algorithms of Oppression: How Search Engines Reinforce Racism. New York: New York University Press.
Parisi, Luciana, and Denise Ferreira da Silva. 2021. "Black Feminist Tools, Critique, and Techno-Poethics", e-flux journal no. 123 (December). https://www.e-flux.com/journal/123/436929/black-feminist-tools-critique-and-techno-poethics/.
Pritchard, Helen. 2018. "Critter Compiler". EXECUTING PRACTICES, 237.
Rogers, Reece. 2023. "How Threads" Privacy Policy Compares to Twitter’s (and Its Rivals’)’. Ars Technica. 8 July 2023. https://arstechnica.com/security/2023/07/how-threads-privacy-policy-compares-to-twitters-and-its-rivals/.
Shelton, Samuel Z. 2020. "Disability Justice, White Supremacy, and Harm Reduction Pedagogy: Enacting Anti-Racist Crip Teaching". JCSCORE 6 (1): 190–208. https://doi.org/10.15763/issn.2642-2387.2020.6.1.190-208.
Sins Invalid. 2015. "10 Principles of Disability Justice". Sins Invalid. 17 September 2015. https://www.sinsinvalid.org/blog/10-principles-of-disability-justice.
Soon, Winnie, and Geoff Cox. 2021. Aesthetic Programming: A Handbook of Software Studies. London: Open Humanities Press.
Suchman, L. 2012. "Configuration". Inventive Methods, 62–74.
Thorndike, Edward L. 1898. "Animal Intelligence: An Experimental Study of the Associative Processes in Animals" The Psychological Review: Monograph Supplements 2 (4): i–109. https://doi.org/10.1037/h0092987.
Tyżlik-Carver, Magdalena, Lozana Rossenova, and Lukas Fuchsgruber. 2022. "Curating/Fermenting Data: Data Workflows for Semantic Web Applications: Curating/Fermenting Data". In Adjunct Proceedings of the 2022 Nordic Human-Computer Interaction Conference, 1–5. Aarhus Denmark: ACM. https://doi.org/10.1145/3547522.3547701.
Digital infrastructures here denote the software, hardware, protocols, systems, and management of digital/computational technology that enable/scope our social digital abilities. This can be cloud drives, word processors, server stacks, local networks, GPS and of course recommender systems.↩
Suchman describes configuration as: “Configuration in this sense is a device for studying technologies with particular attention to the imaginaries and materialities that they join together, an orientation that resonates as well with the term’s common usage to refer to the conjoining of diverse elements in practices of systems design and engineering.” (Suchman 2012)↩
The empowering of people, communities, and their infrastructures through crip wisdom.↩
Shayda Kafai says, “Sins Invalid defines intersectionality this way: ‘Simply put, this principle says that we are many things, and they all impact us. We are not only disabled, we are also each coming from a specific experience of race, class, sexuality, age, religious background, geographic location, immigration status, and more. Depending on context, we all have areas where we experience privilege, as well as areas of oppression... We gratefully embrace the nuance that this principle brings to our lived experiences, and the ways it shapes the perspectives we offer.’"(Kafai 2021, 31)↩
Life affirming infrastructures (not essentially digital) are ones that enable people and communities to explore, share and learn from one another, instead of being prescribed set solutions that delegitimize situated knowledges and lived experiences. This relation implies an ability to form infrastructures outside of extracting, toxic, prescriptive, and rent seeking economies.↩
Examples are Facebook feeds, Instagram reels and TikTok’s for you, YouTube shorts and more.↩
Decentralized here denotes that one organization doesn’t control all the assets of and infrastructure, but it is configured through many nodes/communities.↩
Federated here means a decentralized network where not every node is connected, but where each node dictates how they want to be networked and connect to.↩
Saying this, unfortunately a large number of these platforms are run on AWS, recentralizing them in the hardware of corporate cloud.↩
Unfortunately this example has been recently (within a few days) troubled by Meta’s release of a Twitter clone called Threads, with promises of being federated, which will be interesting to see how they configure it and how the communities deal with Meta’s entrance into their ecologies, but the underlying attitudes of control and extraction are clear from Threads’ terms of service (Rogers 2023).↩
Mastodon allegedly being the origin of content warning blurred images/media, as well as being federated to enable communities to decide which servers they can interact with.↩
Following the work of Ruha Benjamin (2016; 2019), Alexis Pauline Gumbs (2018), M. Jaqui Alexander (2005), and Denise Ferreira da Silva (2014; 2016; 2017), to understand how we can move beyond destructive carceral and segregationist ideologies and implementations within technoscience.↩
The redistribution of cloud infrastructures from corporate to community (Aouragh et al. 2021).↩
The de-embedding of colonial concepts and practices through crip and trans*fem approaches (Kafer 2013; Sins Invalid 2015; Hamraie and Fritsch 2019; Bonhomme et al. 2020; Shelton 2020; Kafai 2021).↩
Large Language Models.↩
As Ferreira da Silva and Parisi put it: “Importantly, this cosmogony must include the myth of Prometheus, as the autopoietic creator and mythical origin of technology for the modern world. As much as this myth corresponds to the belief in human progress, it also ensures that the technology of fire evolves into the steam engine of the modern bio-economic Man, telling the origin story of humanity as one of freedom from enslavement, from the obscurity of the unknown, and from Man’s own death.”(Parisi and Ferreira da Silva 2021)↩
Where unsupervised AI systems form dimensional features that can be extracted and exploited.↩
Denise Ferreira da Silva explains how “first, the 17th century philosophers who called themselves ‘modern’ devised a knowledge program that was concerned with what they called the ‘secondary (efficient) causes’ of motion, which cause change in the appearance of things in nature, and not with the ‘primary (final) causes’ of things, or the purpose (end) of their existence; second, instead of relying on Aristotle’s (384-322 a.C.n.) logical necessity for the assurance of the correctness of their findings, philosophers such as Galileo relied on the necessity characteristic of mathematics, more precisely, on geometrical demonstration as the basis for certainty”(Ferreira da Silva 2016).↩
There are a number of types of loss, but almost all are static, exaggerating forms of comparisons (e.g. squared error).↩
Melt put it as “Access requests explain what a disabled person needs to attend spaces, be they online or physical.”(MELT 2022)↩
Made up of coder/hacker/researchers Yasmin Morgan, Megan Benson, Katie Tindle.↩
Acronym of: Modified National Institute of Standards and Technology (MNIST)↩
A variational autoencoder is a type of unsupervised AI that learns to dimensionally reduce inputs (text, images, etc.) into a latent dimension, to then be decompressed back to its original form.↩